Install Trend Micro Deep Security Agent with Citrix Provisioning services
Today I want to write a short blog to show, how to install Trend Micro Deep Security agent on Citrix PVS target devices the proper way.
First make sure that you already set up a policy in Deep Security Manager (DSM) with the latest AV exclusions recommended by Citrix:
https://www.citrix.com/blogs/2016/12/02/citrix-recommended-antivirus-exclusions/
The configuration is pretty straight forward.
You just have to install the Deep Security Agent (DSA), do some configuration (see below) and make sure the agent will (re-)register itself during boot.
Below you will find the process with the scripts Iam actually using. Nevertheless when you copy&paste make sure you change the variables 🙂
1. Agent installation & configuration
Put your vDisk in maintenance mode (or use versioning if you’re brave) and install the DSA according to Trend Micros suggestions (here):
- Install DSA
- Stop the ‘ds_agent’ service and set the startup type to ‘manual’
- Set the ‘ds_agent’ service to manual
(you have to check in DSM that the machine you’re using for DSA installation have the rights to set the service to manual!) - Remove the files with the following extensions from $Env:ProgramData\Trend Micro\Deep Security Agent\ subdirs:
- *.db
- *.crt
- *.ini
- *.config
- *.bin
B/C we are lazy guys, you can use the following Powershell script to execute all the steps mentioned above.
The script is based on the deployment script you can export in DSM. I slightly modified it according to my needs, make sure you change the variables accordingly…
[code lang=”powershell”]
# This code was created via DSM console, I just modified the code slightly to suit my needs (correct DSM server, x64 windows client, delete the files, etc):
# https://help.deepsecurity.trendmicro.com/Add-Computers/ug-add-dep-scripts.html
# Attention: Make sure to change the variables according to your environment…
# FQDN to your Trend Micro Deep Security Manager
$DSMserver = "dsmserver.domain.tld:4119"
# Download x64 client from DSM server:
$DSAUrl="https://$DSMServer/software/agent/Windows/x86_64/"
# Path for logfile
$env:LogPath = "$env:appdata\Trend Micro\Deep Security Agent\installer"
# InstallDir for DSA
$DSAInstallDir = "C:\Program Files (x86)\Trend Micro"
# Policy ID for your Citrix policy:
$DSAPolicyID = "34"
# Name of DS agent service
$DSAServiceName = "ds_agent"
New-Item -path $env:LogPath -type directory
Start-Transcript -path "$env:LogPath\dsa_deploy.log" -append
echo "$(Get-Date -format T) – DSA download started"
echo "$(Get-Date -format T) – Download Deep Security Agent Package" $DSAUrl
[Net.ServicePointManager]::ServerCertificateValidationCallback = {$true}
(New-Object System.Net.WebClient).DownloadFile($DSAUrl, "$env:temp\agent.msi")
if ( (Get-Item "$env:temp\agent.msi").length -eq 0 ) {
echo "Failed to download the Deep Security Agent. Please check if the package is imported into the Deep Security Manager. "
exit 1 }
echo "$(Get-Date -format T) – Downloaded File Size:" (Get-Item "$env:temp\agent.msi").length
echo "$(Get-Date -format T) – DSA install started, please be patient…"
echo "$(Get-Date -format T) – Installer Exit Code:" (Start-Process -FilePath msiexec -ArgumentList "/i $env:temp\agent.msi /qn TARGETDIR="$DSAInstallDir" ADDLOCAL=ALL /l*v "$env:LogPath\dsa_install.log"" -Wait -PassThru).ExitCode
echo "$(Get-Date -format T) – DSA activation started, this is going to take some time, please be patient"
Start-Sleep -s 50
& $DSAInstallDir"\Deep Security Agent\dsa_control.cmd" -r
& $DSAInstallDir"\Deep Security Agent\dsa_control.cmd" -a dsm://$DSMServer/ "policyid:$DSAPolicyID"
Stop-Transcript
echo "$(Get-Date -format T) – DSA Deployment Finished"
echo "$(Get-Date -format T) – Stopping $DSAServiceName service and setting startup type to manual"
While ((Get-Service -Name $DSAServiceName).Status -ne ‘Stopped’) {
echo "$(Get-Date -format T) – $DSAServiceName service stopped, going to set startup type…"
Set-Service $DSAServiceName -StartupType Manual
Start-Sleep 5
}
echo "$(Get-Date -format T) – Removing some files according to manual…"
Get-ChildItem "$Env:ProgramData\Trend Micro\Deep Security Agent\" -include *.db,*.crt,*.ini,*.config,*.bin -recurse | foreach ($_) {remove-item $_.fullname}
echo "$(Get-Date -format T) – Script finished, good to go…"
[/code]
Now you can go ahead and seal the image like you always do (of course with the great BIS-F).
2. Deep Security Manager configuration
Doublecheck in DSM that you already configured the re-registration of the client, otherwise the agent registration will not work.
Go to “Administration > System Settings > Agents” and make sure the “Agent-initiated Activation” is configured like shown below:

3. GPO to start service and (re-)register agent
Because we have to start the service during boot I decided to use a GPO which will start the service and execute a Powershell script which is doing the (re-)registration of the agent.
Create a GPO (in my case “CTX_VDA_StartAndRegisterTMDSAgent”) with the following settings and link it to the OU with the VDAs:
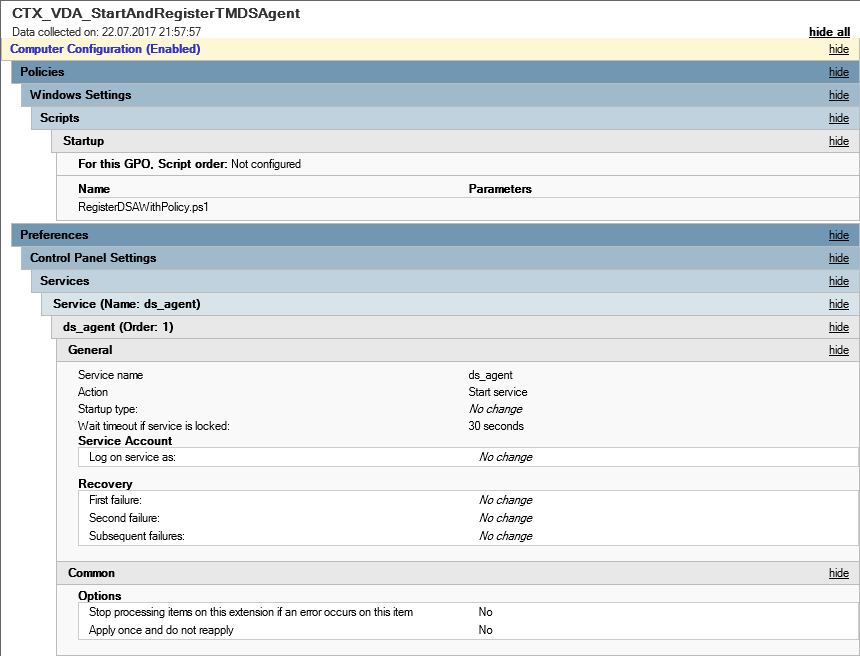
To (re-)register the DSA against DSM you can use “RegisterDSAWithPolicy.ps1″ I created:
[code lang=”powershell”]
<#
.SYNOPSIS
(Re-)Registers Trend Micro Deep Security Agent (DSA) against Trend Micro Deep Security Manager (DSM)
.DESCRIPTION
This script will be fired up by a GPO called "CTX_VDA_StartAndRegisterTMDSAgent" and will (re-)register the DSA against the DSM.
It will automatically assign the correct policy to the computer object
.EXAMPLE
.\RegisterDSAWithPolicy.ps1
.INPUTS
None.
.OUTPUTS
Logfile, see $LogFile variable
.NOTES
Double check that the variables suits your needs.
Make sure the log file will be on a persistent drive.
NAME: RegisterDSAWithPolicy.ps1
VERSION: 1.00
AUTHOR: Markus Zehnle
LASTEDIT: 19.07.2017 #>
#region: variables
# Path to dsa_control.cmd
$DSAControl = ‘${env:ProgramFiles(x86)}\Trend Micro\Deep Security Agent\dsa_control.cmd’
# DeepSecurity Citrix Policy
$PolicyID = ‘policyid:34’
# DeepSecurity Server
$DSServer = ‘dsmserver.domain.tld:4120’
# ServiceName:
$ServiceName = "ds_agent"
# Local Logfile
$LogFile = "D:\LOG\tmdsaregistration.log"
# Computername
$ComputerName = $Env:computername
#endregion: variables
#region: magic
Write-Output "$(Get-Date): Start TrendMicro DeepSecurity Agent registration on $ComputerName" > $LogFile
Write-Output "$(Get-Date): ——————————————————————–" >> $LogFile
Write-Output "$(Get-Date):" >> $LogFile
Write-Output "$(Get-Date): Check if $ServiceName service is running:" >> $LogFile
While ((Get-Service -Name $ServiceName).Status -ne ‘Running’) {
Write-Output "$(Get-Date): $ServiceName service is not running, waiting until it starts…" >> $LogFile
Start-Sleep 5
}
Write-Output "$(Get-Date): $ServiceName service is running, go ahead" >> $LogFile
Write-Output "$(Get-Date): " >> $LogFile
Write-Output "$(Get-Date): Check if $DSAControl exists:" >> $LogFile
If (Test-Path $DSAControl) {
Write-Output "$(Get-Date): $DSAControl exists, lets fire up registration!" >> $LogFile
Write-Output "$(Get-Date):" >> $LogFile
Write-Output "$(Get-Date): $DSAControl -a dsm://$DSServer/ $PolicyID" >> $LogFile
& $DSAControl -a dsm://$DSServer/ $PolicyID >> $LogFile
} else {
Write-Output "$(Get-Date):" >> $LogFile
Write-Output "$(Get-Date): No $DSAControl found! Script will Exit" >> $LogFile
Exit
}
Write-Output "$(Get-Date):" >> $LogFile
Write-Output "$(Get-Date): TrendMicro DeepSecurity Agent registration finished" >> $LogFile
#endregion: magic
[/code]
As usual: Use your brain before putting my scripts in your environment!